EIGRP Authentication
EIGRP authentication is used to prevent an attacker from forming the EIGRP neighbor relationship with your router and advertising incorrect routing information. By using the same preshared key (PSK) on all routers you can force EIGRP to authenticate each EIGRP message. That way you can ensure that your router accepts routing updates only from the trusted sources. To authenticate every message, the MD5 (Message Digest 5) algorithm is used.
Three steps are required to configure EIGRP authentication:
- 1. creating a keychain
- 2. specifying a key string for a key
- 3. configuring EIGRP to use authentication
EIGRP uses the concept of key chains. Each key chain can have many keys, just like in real life. You can specify a different lifetime interval of each key. That way the second key in a key chain can be used after the first one is expired, the third one after the second, and so on. After you have created a key chain with the corresponding keys, you need to enable EIGRP authentication for a particular interface.
To configure a router to use EIGRP configuration the following commands are used:
1. (global-config) key chain NAME – creates a keychain
2. (config-keychain) key NUMBER – identifies the key number
3. (config-keychain-key) key-string STRING – specifies the key string for the key
Next, we need to enable EIGRP authentication on an interface. From the interface mode, the following commands are used:
4. (config-if) ip authentication mode eigrp ASN md5 – enables EIGRP authentication on the interface
5. (config-if) ip authentication key-chain eigrp ASN KEY_CHAIN_NAME – specifies the name of the key chain that will be used for authentication note
For the authentication to work, the key number and the key string have to match on both routers! The key chain name doesn’t have to be the same on both routers.
The following example shows how EIGRP authentication is configured:

To establish a time frame for the validity of a key, you need to configure the accept-lifetime and the send-lifetime parameters. The syntax of the commands is:
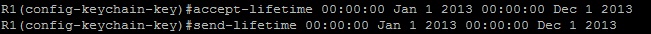
(config-keychain-key) accept-lifetime start_time {infinite | end_time | duration seconds}
(config-keychain-key) send-lifetime start_time {infinite | end_time | duration seconds}The first command specifies the time period during which the key will be accepted. The second command specifies the time period during which the key will be sent.
For example, if we want to use a key only from January 1st, 2013 to December 1st, 2013, the following commands are used:
EIGRP Load-Balancing
By default, EIGRP supports equal-cost load balancing over four links. Equal-cost means that multiple routes must have the same metric to reach the destination, so that router can choose to load balance across equal cost links.
To better understand the equal-cost load balancing concept, consider the following example.

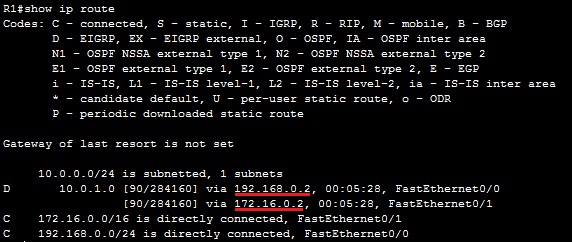
All three routers are running EIGRP. Routers R2 and R3 are connected to the subnet 10.0.1.0/24. Both routers advertise the route to reach that subnet to R1. Router R1 receives the two routing updates for the subnet 10.0.1.0/24 with the same metric (the metric is the same because both routers connect to the subnet 10.0.1.0/24 and R1 across the links with the same bandwidth and delay values). Router R1 places both routes in the routing table and load balances across three links.
You can verify that R1 is indeed using both paths by typing the show ip route command:
One of the advantages of EIGRP is that, unlike OSPF and many other routing protocols, EIGRP also supports unequal-cost load balancing. You can set up your router to load balance over links with a different metric to reach the destination. To accomplish unequal-cost load balancing, the variance command is used. The command takes one parameter, the multiplier, which tells the router to load balance across each link with the metric for the destination less than the feasible distance multiplied by the multiplier value.NOTE
The multiplier value, by default, is 1. The maximum value is 128.
Consider the following example.
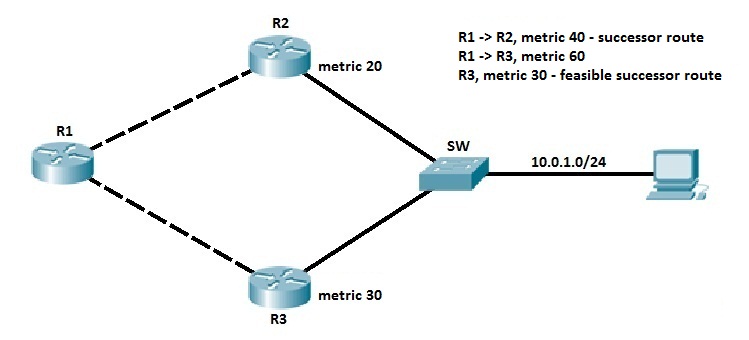
All three routers are running EIGRP. Routers R2 and R3 are connected to the subnet 10.0.1.0/24. Both routers advertise the route to reach that subnet to R1. Router R1 chooses the route from R2 as the best route. Let’s say that R1 calculated the metric of 40 for the path through R2. That route is placed in the R1’s routing table. But what if we want to load balance traffic across the other link? The route through R3 has a feasible distance of 30, which is less than the metric of the successor route, so the feasibility condition has been met and that route has been placed in the R1’s topology table. Let’s say that R1 calculated the metric of 60 for the route through R3. To enable load balancing across that link, you need to use the variance command:
(router-eigrp) variance MULTIPLIER
In our example, variance 2 commands can be used. This tells the router to load balance across any links with the metric less than 80 (because 40 times 2 is 80). The route through R3 is added to the routing table.NOTE
A path has to be a feasible successor route to be used in unequal load balancing.
EIGRP Reliable Transport Protocol (RTP)
EIGRP doesn’t send messages with UDP or TCP; instead, a Cisco’s protocol called Reliable Transport Protocol (RTP) is used for communication between EIGRP-speaking routers. As the name implies, reliability is a key feature of this protocol, and it is designed to enable quick delivery of updates and tracking of data reception.
Five different packets types are used by EIGRP:
- Update – contains route information. When routing updates are sent in response to the metric or topology changes, reliable multicasts are used. In the event that only one router needs an update, for example when a new neighbor is discovered, unicasts are used.
- Query – a request for specific routes that always uses the reliable multicast method. Routers send queries when they realize they’ve lost the path to a particular network and are looking for alternative paths.
- Reply – sent in response to a query via the unicast method. Replies can include a specific route to the queried destination or declare that there is no known route.
- Hello – used to discover EIGRP neighbors. It is sent via unreliable multicast and no acknowledgment is required.
- Acknowledgment (ACK) – sent in response to an update and is always unicast. ACKs are not sent reliably.
NOTE
The acronym RTP is also used for a different protocol – Real-time Transport Protocol (RTP), used for VoIP communication.
EIGRP Diffusing Update Algorithm (DUAL)
Diffusing Update Algorithm (DUAL) is an algorithm used by EIGRP to select and maintain the best route to each remote network. DUAL is also used for the following purposes:
- discover a backup route if there is one available.
- support for variable-length subnet masks (VLSMs).
- perform dynamic route recoveries.
- query neighbors for unknown alternate routes.
- send out queries for alternate routes.
EIGRP stores all routes advertised by all EIGRP neighbors. The metric of these routes is used by DUAL to select the efficient and loop-free paths. DUAL selects routes that will be inserted into the routing table. If a route fails, and there is no feasible successor, DUAL chooses a replacement route, which usually takes a couple of seconds.
The following requirements must be met in order for DUAL to work properly:
- EIGRP neighbors must discover.
- all transmitted EIGRP messages should be received correctly.
- all changes and messages should be processed in the order in which they’re detected.
EIGRP summary
Here is a list of the most important EIGRP features:
- advanced distance vector routing protocol
- classless routing protocol
- supports VLSM (Variable Length Subnet Mask)
- converges fast
- supports multiple Network layer protocols (IPv4, IPv6, IPX, AppleTalk…)
- uses multicast address of 224.0.0.10 for routing updates
- sends partial routing updates
- supports equal and unequal-cost load balancing
- supports manual summarization on any router within a network
- by default, uses bandwidth and delay to calculate its metric
- Cisco proprietary
- supports MD5 authentication